Digital forensic investigation
Data: 2.03.2018 / Rating: 4.7 / Views: 733Gallery of Video:
Gallery of Images:
Digital forensic investigation
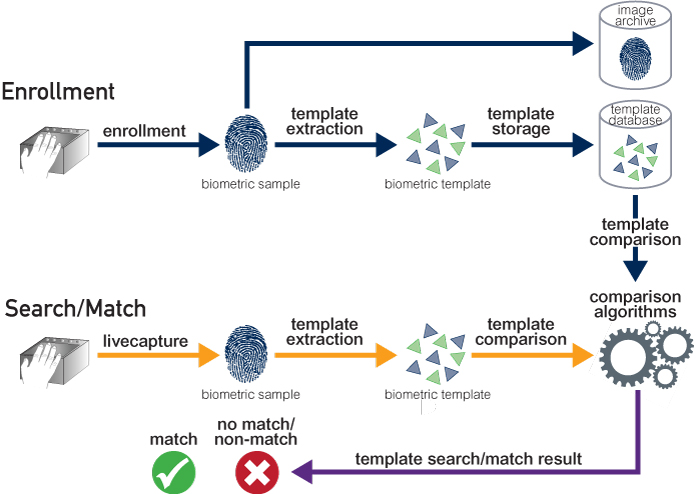
SANS Digital Forensics and Incident Response Blog blog pertaining to Intro to Report Writing for Digital Forensics. As digital forensic examinersanalysts, we must report and present our findings on a very technical discipline in a simplistic manner. This is the most detailed section of your investigation. You will include all artifacts. Computer forensic investigators and digital forensic experts who choose to work for private industries and investigative firms generally do so on a contractual basis, which means work may not be as regular or steady. If you enjoy problemsolving and investigation, and you are skilled not only in using a computer but also in digging deep. DIGITAL FORENSIC RESEARCH CONFERENCE The Enhanced Digital Investigation Process Model By Venansius Baryamureeba, Florence Tushabe From the proceedings of Alert Digital forensic investigation framework (DFIF), map, forensic 1. Introduction Since its inception, the field of digital forensic has not been significantly changed. It originates in solving pragmatic acquisition and chain of evidence problems The MSc in Digital Investigation and Forensic Computing from University College Dublin is designed for information technology specialists who need to Digital forensic methodology is preferred to be processed or executed by the information security office. It is because all the other methodologies, like computer forensic, mobile forensic, network forensic and data recovery can give partial investigation results rather than complete investigation of the source of the compromise, as these are all the sub branches of the digital forensic. SANS Computer Forensics Training Community: discover computer forensic tools and techniques for eDiscovery, investigation and incident response. A question I often get asked relating to Digital Forensic and Investigation Capabilities is what tools are required? a question which is both easy, and difficult to answer. Easy, because the answer is everything you need to accomplish the task. Hard because, it is dependent on two factors which are as follows: The level. Digital forensics (sometimes known as digital forensic science) is a branch of forensic science encompassing the recovery and investigation of material found. The digital forensic investigation consulting market is crowded. Security and risk management leaders should use this Market Guide to identify and evaluate the DFI consultancies in this landscape. The digital forensic process is a recognized scientific and forensic process used in digital forensics investigations. [1 [2 Forensics researcher Eoghan Casey defines it as a number of steps from the original incident alert through to reporting of findings. [3 Current Challenges In Digital Forensics Posted by scar May 11, 2016 1 Comment Filed Under challenges in digital forensics, cloud forensics, data triage, dfir, Digital Forensics, encryption, forensic investigation, incident response, investigations SRM's dedicated computer forensics division provides expert digital forensic investigation services and unimpeachable expert witness testimony. 1 eDiscovery in digital forensic investigations 1 Summary Digital information, such as that found on computers, mobile devices and storage media can be And finally, PlainSight is a live CD that allows you to perform forensic tasks such as looking into Internet histories, gathering data on USB device usage, extracting password hashes and others. This paper has proposed a process model for forensic investigation of cloud storage services, and also described some important elements of an investigation. This paper has described a previously unknown method for forensic analysis of cloud storage services for. DIGITAL FORENSIC RESEARCH CONFERENCE An EventBased Digital Forensic Investigation Framework By Brian Carrier, Eugene Spafford From the proceedings of Kent, K. al, (2006) developed a basic digital forensic investigation model called the Four Step Forensics Process (FSFP) with the idea of Venter (2006) that digital forensics investigation can be conducted by even nontechnical persons. Digital Forensics Analysis Report Delivered to Alliance Defending Freedom November 5, 2015 Prepared by Coalfire Systems, Inc. Revision Summary examined using industrystandard forensic tools and techniques. The flash drive contained (i) a total of ten (10) videos International Journal of Computer Science Information Technology (IJCSIT), Vol 3, No 3, June 2011 number of new and improved computer forensic investigation processes have been developed. In this Integrated Digital Investigation Process (IDIP) (2003). Digital Forensics and Cybersecurity Option Parttime Bachelor of Students will learn advanced concepts in digital forensic analysis and investigation. The course will cover the investigation and response process from the focus of a computer forensics analyst. The Digital Forensics and Cybersecurity Option is intended to provide the. The Forensic Report is the most important part of a digital forensic investigation. If a full investigation is completed, this report will be the evidence you need to submit in court. Expert Testimony Certified Forensic Investigation Practitioner (CFIP) Core level course This corelevel technical course is designed for people looking to develop their computer forensics investigation skills, either for a career in digital investigations or as part of their current cyber role. EUROFINS FORENSIC SERVICES' digital investigation and questioned document teams specialise in identifying and realising evidence hidden among traditional document sources, computers, mobile phones and other data storage devices. As experts in Digital Forensic, we secure, analyze, recover and investigate electronic data and eDiscovery Digital Investigation covers a broad array of subjects related to crime and security throughout the computerized world. The primary pillar of this Intrusion investigation is a specialized subset of digital forensic investigation that is focused on determining the nature and full extent of unauthorized access and. The goal of Computer forensics is to perform crime investigations by using evidence from digital data to find who was the responsible for that particular crime. For better research and investigation, developers have created many computer forensics tools. 23 FREE Forensic Investigation Tools for IT Security Expert. Geekflare Blog post is sponsored by Netsparker Web Application Security Scanner. by Chandan Kumar February 17, 2018 Autopsy is a GUIbased open source digital forensic program to analyze hard drives and smart phones efficiently. Autospy is used by thousands of users worldwide to. Digital forensics is the process of uncovering and interpreting electronic data. The goal of the process is to preserve any evidence in its most original form while performing a structured investigation by collecting, identifying and validating the digital information for the purpose of reconstructing past events. Here are 20 of the best free tools that will help you conduct a digital forensic investigation. Whether it's for an internal human resources case, an investigation into unauthorized access to a server, or if you just want to learn a new skill, these suites a perfect place to start. Challenges with Automation in Digital Forensic Investigations Joshua I. James and Pavel Gladyshev joshua. james, Digital Forensic Investigation Research Group Basic Digital Forensic Investigation Concepts. A digital investigation is a process to answer questions about digital states and events. The basic digital investigation process frequenty occurs by all computer users when they, for. In particular, a digital forensic investigation is a process that uses science and technology to examine digital objects and that develops and tests theories, which can be entered into a court of law, to answer questions about events that occurred. A typical analysis on a single device, without any of the above complications (ie. encryption, use of forensic tools, broad scope of investigation work, etc. ) will generally take 1530 hours of work. In our opinion, digital forensic services based on Time Materials approach can easily inflate and end up costing considerably more than what. Your Data and Evidence Acquisition service includes the acquisition of your data and a Preliminary Report provided by the digital forensic examiner after up to 2 hrs of processing and investigation. This is designed to help you decide if a full digital forensic investigation is warranted. Computer Forensic Investigations: Tools and Techniques Forensic specialists investigating computer crimes require a set of dedicated tools as well as the use of very specific techniques. Depending on the type of computer device and the kind of digital evidence, investigators may choose one tool or another. eForensik is a South African digital forensic consultancy specialising in computer forensics, incident response, mobile forensics, eDiscovery and data recovery with offices in Cape Town and Johannesburg. Abstract Digital forensic investigation is termed as the investigation of perceiving, isolating separating and demonstrating the propelled affirmation that has been secured in a large portion of the automated devices across the globe. The various computerized apparatus is now being utilized in the process of making sure that all forensic equipment is well coordinated. Creating a digital evidence forensic unit. Defense Computer Investigation Training Program Linthicum, Maryland Chris Stippich Digital Intelligence, Inc. Waukesha, Wisconsin TWGEDE members Additional members were then incorporated into the TWGEDE to provide a full tech Four Steps to Perform Digital Forensic Investigation with Belkasoft Acquisition Analysis Suite Step One: Capturing a Live RAM dump. This essential first step is often omitted. Yet, we strongly believe that any digital investigation must begin with acquiring a memory dump. Considering the rapidly growing popularity of whole volume encryption. Digital evidence is information stored or transmitted in binary form that may be relied on in court. It can be found on a computer hard drive, a mobile phone, a personal digital assistant (PDA), a CD, and a flash card in a digital camera, among other The Master of Science in digital forensics and cyber investigation at University of Maryland University College is designed to prepare you to meet the growing demand for investigative, leadership, and executive skill in evaluating and managing complex cybersecurity incidents and threats. A forensic investigation has to be conducted in a scientific manner and must comply with all legal requirements, as set out in the second definition of forensics above. Evidence will have to be collected in this ma nner irrespective of the purpose i. internal Computer Forensics and Investigation Methodology 8 steps Also is important to consider that a computer forensic investigation goes hand in hand with computer incident handling and is normally a breakoff point of the containment phase. Digital Forensics Artifacts of interactive sessions. Computer forensics (also known as computer forensic science) is a branch of digital forensic science pertaining to evidence found in computers and digital storage media. The goal of computer forensics is to examine digital media in a forensically sound manner with the aim of identifying, preserving, recovering, analyzing and presenting facts. Cyber Forensic Investigation Plan. DIGITAL FORENSIC TOOL The FTK Imager (2001, guide no. 3) forensic computer tools have changed from command line environment to easy and handy graphical user interface based tools for the sophisticated usage with very useful and informative user manuals for the ease of usage. Evaluation of Digital Forensic Process Models with Respect to Digital Forensics as a Service Xiaoyu Du, NhienAn LeKhac, Mark Scanlon various of problems commonly encountered in the forensic investigation. In the last decade, cloud computing the process of digital forensic investigation, DFaaS could bring several improvements over the. Forensic Control's simple guide to Computer Forensics for beginners. Ideal for lawyers, students and anyone with an interest in this fascinating subject. the concepts apply to any device capable of storing digital information. meaning that at all stages of a computer forensic investigation admissibility should be at the forefront of the
Related Images:
- Ghetto klown john leguizamo
- Black panther v4
- Save private ryan
- Soul eater battle resonance
- Naked and afraid season 2
- The abyss uncut
- Sakurasou no pet na kanojo vostfr
- Call the midwife
- Middlesex by Jeffrey Eugenides
- Make report php
- Tagging That Ass
- Graceland s01e04 720p
- Evil angel 4 21
- Internet security swedish
- Casino jack and the united states of money
- Escape from camp14
- Snow of kili
- In search of blind joe death
- Supernatural season 1 episode 1 11
- B b roman
- Road kill episode
- Learn slr photography
- Flac ost 2013
- Neil gaiman the ocean
- The conjuring hindi
- Maroon 5 latest
- Big brother s
- Jump music video
- Friends with kids 2011 720p
- Eminem sing for
- 5 degrees of separation
- The rough guide to bollywood
- Peter kay pop
- Autodesk autocad architecture 2014
- People vs larry flint
- Virus windows server
- Frisell blues dream
- Thundercats The Complete Series
- Massive presets edm
- Force of execution 2013 720p bluray x264 rovers
- Love in school
- Fantasy all stars
- Buz devri 1
- Vampire diaries s06e04 1080p
- Dieter need to fly
- The quest s01e
- Here to stay korn
- Magic english ita
- The big bang theory 8x06
- Wonder woman 720
- Counter strike global offensive no steam
- Australia vs pakistan
- How the universe works
- Charles bronson french
- Poker serie bluf
- Key of c
- Passenger little light
- Sexual predator 2001 uncut
- Breaking bad season 2 nl subs
- Fhm philippines december 2011
- Masters of horror cigarette burns
- Kick 1080p 51
- Welcome To New York 2014 720p
- Extensions all in one
- Pirates caribbean psp
- Si enteng kabisote
- Into the storm yify
- Binbou shimai monogatari
- Angelina chung jennifer dark
- 720p bluray ac3 x264
- Prince game for pc
- The Rules of
- The amazing spid man 2
- Pat benatar 320
- Damn shorty got a thicky thick
- Vintage cafe lounge jazz blends special selection
- Code of the Forgotten Eight
- The texas chainsaw massacre 1080